CLIENT/SERVER TECHNOLOGY:FUNDAMENTAL TECHNOLOGIES FOR C / S SYSTEMS
4. FUNDAMENTAL TECHNOLOGIES FOR C / S SYSTEMS
Communication Methods
The communication method facilitating interactions between a client and a server is the most im- portant part of a C / S system. For easy development of the C / S systems, it is important for processes located on physically distributed computers to be seen as if they were placed in the same machine. Socket, remote procedure call, and CORBA are the main interfaces that realize such transparent communications between distributed processes.
Socket
The socket interface, developed as the communication port of Berkeley UNIX, is an API that enables communications between processes through networks like input / output access to a local file. Com- munications between two processes by using the socket interface are realized by the following steps (see Figure 8):
1. For two processes in different computers to communicate with each other, a communication port on each computer must be created beforehand by using ‘‘socket’’ system call.
2. Each socket is given a unique name to recognize the communication partner by using ‘‘bind’’ system call. The named socket is registered to the system.
3. At the server process, the socket is prepared for communication and it is shown that the server process is possible to accept communication by using ‘‘listen’’ system call.
5. The communication request from the client process is accepted by using ‘‘accept’’ system call in the server process. Then the connection between the client process and the server process is established.
6. Finally, each process begins communicating mutually by using ‘‘read’’ or ‘‘write’’ system calls.
Remote Procedure Call
Because the application programming interface (API) for socket programming uses system calls, the overhead associated with an application that communicates through the socket interface is rather small. However, because API is very primitive, socket programming depends on operating systems and the development of a system with a socket interface becomes complicated. For example, where programmers develop a system in which communications between processes on different platforms (such as Windows and UNIX) are required, they should master several versions of socket API sup- ported by each platform.
One of the earliest approaches to facilitating easier use of sockets is realized by a remote procedure call (RPC). An RPC is a mechanism that lets a program call a procedure located on a remote server in the same fashion as a local one within the same program. It provides a function-oriented interface, and necessary preparation for communication is offered beforehand. An RPC is realized by a mech- anism called a stub. The functions of stubs at client and server sides are to mimic the missing code, convert the procedure’s parameters into messages suitable for transmission across the network (a process called marshaling) and unmarshal the parameters to a procedure, and dispatch incoming calls to the appropriate procedure.
Communications between two processes by using an RPC is realized by the following steps (see Figure 9):
1. The client program invokes a remote procedure function called the client stub.
2. The client stub packages (marshals) the procedure’s parameters in several RPC messages and uses the runtime library to send them to the server.
3. At the server, the server stub unpacks (unmarshals) the parameters and invokes the requested procedure.
4. The procedure processes the request.
5. The results are sent back to the client through the stubs on both sides that perform the reverse processing.
The sequence from 1 to 5 is concealed from application programmers. One of the advantages of an RPC is that it hides the intricacies of the network and these procedures behave much the same as ordinary procedures to application programmers.
CORBA
An object is an entity that encapsulates data and provides one or more operations (methods) acting on those data; for example, ‘‘the bank object’’ has data from his client’s account and operations by
which to manipulate them. Object-oriented computing is enabling faster software development by promoting software reusability, interoperability, and portability. In addition to enhancing the produc- tivity of application developers, object frameworks are being used for data management, enterprise modeling, and system and network management. When objects are distributed, it is necessary to enable communications among distributed objects.
The Object Management Group, a consortium of object technology vendors founded in 1989, created a technology specification named CORBA (Common Object Request Broker Architecture). CORBA employs an abstraction similar to that of RPC, with a slight modification that simplifies programming and maintenance and increases extensibility of products.
The basic service provided by CORBA is delivery of requests from the client to the server and delivery of responses to the client. This service is realized by using a message broker for objects, called object request broker (ORB). An ORB is the central component of CORBA and handles distribution of messages between objects. Using an ORB, client objects can transparently make requests to (and receive responses from) server objects, which may be on the same computer or across a network.
An ORB consists of several logically distinct components, as shown in Figure 10.
The Interface Definition Language (IDL) is used to specify the interfaces of the ORB as well as services that objects make available to clients. The job of the IDL stub and skeleton is to hide the details of the underlying ORB from application programmers, making remote invocation look similar to local invocation. The dynamic invocation interface (DII) provides clients with an alternative to using IDL stubs when invoking an object. Because in general the stub routine is specific to a particular operation on a particular object, the client must know about the server object in detail. On the other hand, the DII allows the client to dynamically invoke a operation on a remote object. The object adapter provides an abstraction mechanism for removing the details of object implementation from the messaging substrate: generation and destruction of objects, activation and deactivation of objects, and invocation of objects through the IDL skeleton.
When a client invokes an operation on an object, the client must identify the target object. The ORB is responsible for locating the object, preparing it to receive the request, and passing the data needed for the request to the object. Object references are used for the ORB of the client side to identify the target object. Once the object has executed the operation identified by the request, if there is a reply needed, the ORB is responsible for returning the reply to the client.
The communication process between a client object and a server object via the ORB is shown in Figure 11.
1. A service request invoked by the client object is handled locally by the client stub. At this time, it looks to the client as if the stub were the actual target server object.
2. The stub and the ORB then cooperate to transmit the request to the remote server object.
3. At the server side, an instance of the skeleton instantiated and activated by the object adapter is waiting for the client’s request. On receipt of the request from the ORB, the skeleton passes the request to the server object.
4. Then the server object executes the requested operations and creates a reply if necessary.
5. Finally, the reply is sent back to the client through the skeleton and the ORB that perform the reverse processing.
The main features of the CORBA are as follows:
1. Platform independence: Before the ORB transmits the message (request or result) from the client object or the server object into the network, the ORB translates the operation and its parameters into the common message format suitable for sending to the server. This is called marshaling. The inverse process of translating the data is called unmarshaling. This mechanism realizes communications between objects on different platforms. For example, a client object implemented on the Windows operating system can communicate with a server object imple- mented on the UNIX operating system.
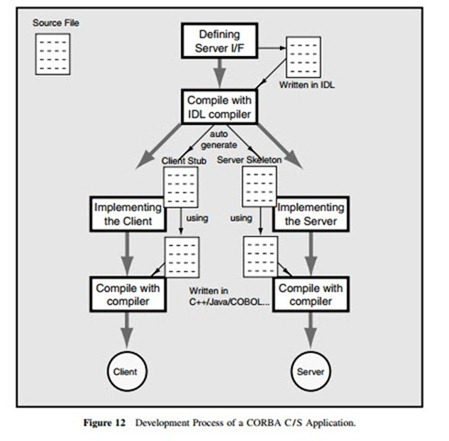
2. Language independence: Figure 12 shows the development process of a CORBA C / S appli- cation. The first step of developing the CORBA object is to define the interface of the object (type of parameters and return values) by using the intermediate language IDL. Then the definition file described in IDL is translated into the file containing rough program codes in various development languages such as C, C++, Java, and COBOL.
IDL is not a programming language but a specification language. It provides language indepen- dence for programmers. The mapping of IDL to various development languages is defined by OMG. Therefore, a developer can choose the most appropriate one from various development languages to implement objects. Also, this language independence feature enables the system to interconnect with legacy systems developed by various languages in the past.
Other Communication Methods
In addition to Socket, RPC, and CORBA, there are several methods for realizing communication between processes.
• Java RMI (remote method invocation) is offered as a part of the JAVA language specification and will be a language-dependent method for the distributed object environment. Although there is the constraint that all the environments should be unified into Java, the developing process with it is a little easier than with CORBA or RPC because several functions for distributed computing are offered as utility objects.
• DCOM (distributed component object model) is the ORB that Microsoft promotes. A DCOM is implemented on the Windows operating system, and the development of applications can be practiced by using a Microsoft development environment such as Visual Basic.
Distributed Transaction Management
In a computer system, a transaction consists of an arbitrary sequence of operations. From a business point of view, a transaction is an action that involves change in the state of some recorded information related to the business. Transaction services are offered on both file systems and database systems.
The transaction must have the four properties referred to by the acronym ACID: atomicity, con- sistency, isolation, and durability:
• Atomicity means that all the operations of the transaction succeed or they all fail. If the client or the server fails during a transaction, the transaction must appear to have either completed successfully or failed completely.
• Consistency means that after a transaction is executed, it must leave the system in a correct state or it must abort, leaving the state as it was before the execution began.
• Isolation means that operations of a transaction are not affected by other transactions that are executed concurrently, as if the separate transactions had been executed one at a time. The transaction must serialize all accesses to shared resources and guarantee that concurrent pro- grams will not affect each other’s operations.
• Durability means that the effect of a transaction’s execution is permanent after it completes commitments. Its changes should survive system failures.
The transaction processing should ensure that either all the operations of the transaction complete successfully (commit) or none of them commit. For example, consider a case in which a customer transfers money from an account A to another account B in a banking system. If the account A and the account B are registered in two separate databases at different sites, both the withdrawal from account A and the deposit in account B must commit together. If the database crashes while the updates are processing, then the system must be able to recover. In the recovery procedure, both the updates must be stopped or aborted and the state of both the databases must be restored to the state before the transaction began. This procedure is called rollback.
In a distributed transaction system, a distributed transaction is composed of several operations involving distributed resources. The management of distributed transactions is provided by a trans- action processing monitor (TP monitor), an application that coordinates resources that are provided by other resources.
A TP monitor provides the following management functions:
• Resource management: it starts transactions, regulates their accesses to shared resources, mon- itors their execution, and balances their workloads.
• Transaction management: It guarantees the ACID properties to all operations that run under its protection.
• Client / server communications management: It provides communications between clients and servers and between servers in various ways, including conversations, request-response, RPC, queueing, and batch.
Available TP monitor products include IBM’s CICS and IMS / TP and BEA’s Tuxedo.
Distributed Data Management
A database contains data that may be shared between many users or user applications. Sometimes there may be demands for concurrent sharing of the data. For example, consider two simultaneous accesses to an inventory data in a multiple-transaction system by two users. No problem arises if each demand is to read a record, but difficulties occur if both users attempt to modify (write) the record at the same time. Figure 13 shows the inconsistency that arises when two updates on the same data are processed at nearly the same time.
The database management must be responsible for this concurrent usage and offer concurrency control to keep the data consistent. Concurrency control is achieved by serializing multiple transac- tions through use of some mechanism such as locking or timestamp.
Also, in case the client or the server fails during a transaction due to a database crash or a network failure, the transaction must be able to recover. Either the transaction must be reversed or else some previous version of the data must be available. That is, the transaction must be rolled back. ‘‘All conditions are treated as transient and can be rolled back anytime’’ is the fundamental policy of control in the data management.
In some C / S systems, distributed databases are adopted as database systems. A distributed da- tabase is a collection of data that belong logically to the same system but are spread over several sites of a network. The main advantage of distributed databases is that they allow access to remote data transparently while keeping most of the data local to the applications that actually use it.
The primary concern of transaction processing is to maintain the consistency of the distributed database. To ensure the consistency of data at remote sites, a two-phase commit protocol is sometimes used in a distributed database environment. The first phase of the protocol is the preparation phase, in which the coordinator site sends a message to each participant site to prepare for commitment. The second phase is the implementation phase, in which the coordinator site sends either an abort or a commit message to all the participant sites, depending on the responses from all the participant sites. Finally, all the participant sites respond by carrying out the action and sending an acknowl- edgement message. Because the commitment may fail in a certain site even if commitments are completed in other sites, in the first phase of the two phase commit protocol, temporary ‘‘secure’’ commitment that can be rolled back anytime is done at each site. After it is confirmed that all the sites succeeded, the ‘‘official’’ commitment is performed.
The two-phase commit protocol has some limitations. One is the performance overhead that is introduced by all the message exchanges. If the remote sites are distributed over a wide area network, the response time could suffer further. The two-phase commit is also very sensitive to the availability of all sites at the time of update, and even a single point of failure could jeopardize the entire transaction. Therefore, decisions should be based on the business needs and the trade-off between the cost of maintaining the data on a single site and the cost of the two-phase commit when data are distributed at remote sites.







Comments
Post a Comment